NetApp Inc is an American company in the field of Computer Storage and Data Management. It is listed in the Fortune 500 companies.
NetApp was the first to reach the market with enterprise-ready, unified scale-out storage in the form of NetApp Clustered Data ONTAP. This essentially lets you take NetApp storage arrays and cluster them together to form a virtualized shared storage pool.
Scale-Up Vs Scale-Out Storage
All storage controllers have a physical limit to which they can be expanded, eg – number of CPUs, memory slots, space for disk shelves. Once the limit for these has been reached and the controller is completely populated the only option is to aquire one or more additional controller. This is called as “scale-up” where you replace your existing controller with one with newer technology or you run multiple controllers side by side. Scaling-up increases the operational burden as the environment grows. Eg – When you replace a controller with a new one, then data migration is needed which is time consuming, often disruptive and complex. If you use 2 or more controllers then you need tools for load balancing them.
With “scale-out” you can seamlessly add controllers to your resource pool which resides on a virtualized shared storage. NetApp provides this storage virtualization and using scale-out, you can move host & client connection, data stores non disruptively anywhere in the resource pool. And all this can be achieved while your environment is online and serving data, without any downtime!
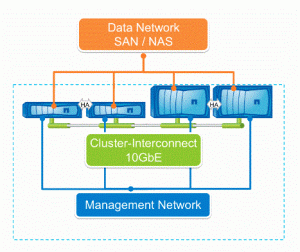
Clustered Data ONTAP Architecture
The basic building block is a high availability (HA) pair which consists of 2 identical nodes. The nodes are connected using redundant cabled network paths. When one node goes down, the other takes over its storage ans maintains access to its data. When the downed system rejoins the cluster, the partner node gives back the storage resources. The minimum cluster size starts with 2 nodes in an HA pair. Using non-disruptive technology refresh, the cluster can evolve to the largest cluster size and powerful hardware.
VServer / Virtual Array
The storage array that resides on top of the available hardware. It maps to the IP address, hostname and/or the fiber channel addresses they attach to. Mapping a LUN is done through vserver. A file share or export is mapped ot mounted via the vserver.
LIFs
These are logical interfaces or virtual adapters that can share the same physical interfaces or be placed on dedicated interfaces.
Cluster Virtualization
Storage Efficiency and Data Protection
Storage efficiency built into clustered Data ONTAP offers substantial space savings, allowing more data to be stored at lower cost. Data protection provides replication services, so valuable data is backed up and recoverable.
Thin Provisioning
Volumes are created using virtual sizing. All the storage is not pre-allocated upfront. The space is unused until data is written to the volume, and only that much space is used as needed by the data. The unused storage is shared across all volumes.
Deduplication
Deduplication removes duplicate data blocks in primary & secondary storage. It stores only unique blocks. Deduplication run can be customized.
Compression
Compression is achieved using algo which replaces repeating patterns within a subset of a file.